System set-up
System Set-up
Password Check system consists of a webserver, Password Check application and a database.
Webserver
The webserver is the interface with the user. It provides Password Check, administers the statistics in a database and hosts the website.
Password Check application
Password Check is the core application that assesses the strength of an inputted password. Password Check is implemented in JavaScript. JavaScript programmes are executed by the browser on the user’s computer. This means that no passwords or other private user data is sent to the server. All computations take place on the user’s computer. When the browser is closed the data is deleted. To obtain a statistic on the frequency of strong and weak passwords, the JavaScript program sends the results to the server. The only information that is transmitted is whether the result is strong or weak.
Password checking is described in Checking Process.
Database
The database collects information on the quality of the verified password (strong / weak) for statistics.
Solely the results of the check are stored. Passwords are never transmitted to the server.
Checking Process
Password Check process assesses the strength of a password, based on the probability of the number of attempts required by an attacker to figure it out. First and foremost, this depends on the length of the password and the number of characters used in the set.
If a password contains known words, number sequences or keyboards patterns, these can be useful to an attacker. Instead of trying out long and random strings, the attacker will first attempt combinations of dictionary words, year numerals, keyboard patterns and so forth. This greatly reduces the number of required attempts.
Password Check will look for the following elements:
- words from German, French, Italian, Romansch and English dictionaries (as selected by the user)
- Swiss keyboard patterns (for example, «qwertz»)
- sequential numbers and alphabetical sequences (for example «1234», «abcd»)
- dates (for example, «03.06.2019»)
By searching in the dictionary, amended upper and lower case letters and l33t-letters can be recognised. For example, c@t, hOUse and b3d are found as words.
Password Check calculates the theoretical number of combination attempts that are needed to find out a password. First of all, the aforementioned dictionary words and patterns are searched for inx1 the password and then the password is broken down into its component parts.
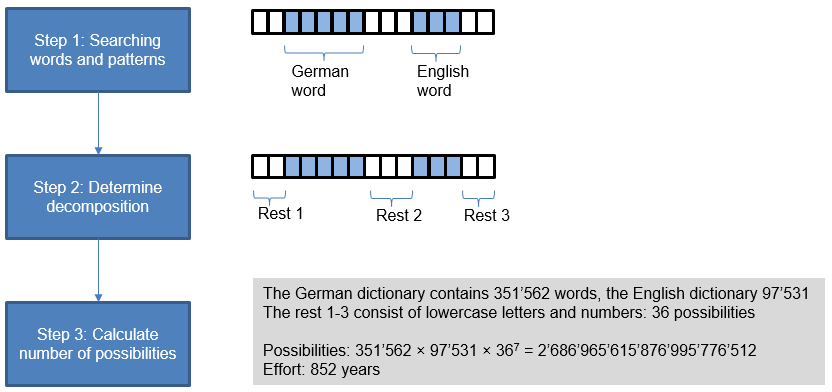
A calculation is made for each substring of how many attempts an attacker would need:
- By using words from the activated dictionaries, the number of possibilities is equal to the size of the dictionary. Based on recognition of upper and lower case letters as well as l33t, the size of the actual dictionary increases by a factor of 10.
- Keyboard patterns, sequential numbers and alphabetical results: the number of possible combinations.
- For any other characters that are not part of a word or pattern, kn represents the number of possibilities, whereby k is the number of possible characters and n is the length.
To estimate the effort in time, it is assumed that an attacker can make a billion attempts per second. This corresponds to the processing power of high-performance PCs with specialised soft- and hardware.
A password has to withstand an attack with a computing time of more than a year to be judged to be strong.
Cracking Passwords
The simplest method of cracking a password is to try out all possibilities in sequence. This method is very laborious, as number of attempts needed increases exponentially with the length of the password.
As most people do not select their passwords at random, ambitious tools try to crack the passwords by using specialised password dictionaries. Moreover, as well as the usual words found in any dictionary, password dictionaries also contain useful character sequences such as keyboard patterns, or sequential numbers such as 12345. These may include letters that are often substituted by other characters, for example E by 3 or A by @ - which is also known as leet / leetspeak. The use of password dictionaries and inclusion of leet considerably lessens the number of attack attempts needed.
On-line and off-line attacks proceed differently. If, for example, an authorised person has access to a laptop, then this person can make a copy of the hard drive and then try out billions of potential passwords on their own computer. Password Check assumes that the attacker is able to make a billion attempts per second.
Even on-line services can be victims of an off-line attack. If someone is able to make a copy of the password database, then they are able to make a good number of attempts per second using their own computer.
The theft of password databases is also problematic for another reason: these databases often contain other user data, such as names and email addresses. Since many users employ the same password for several services, attackers try to log in to other services using stolen email and password data.
What does Password Check do?
What it does
Password Check checks the password against commonplace character sequences that any attacker might expect, thereby simplifying things greatly for the attacker. This includes dictionary words, keyboard patterns, sequential numbers etc.
An assessment of the search effort is undertaken, based on the character sequences that have been found.
Details of the evaluation process can be found in Checking Process.
What Password Check does not do
The risks of targeted searches cannot be covered by a generic Password Check. Password Check works in tandem with general dictionaries. These include frequent names in various languages. An attacker with a specific victim in sight is able to draw on knowledge about that person: date of birth, surname, address, family information, names of children of pets etc.
Password Check cannot take into account the risk that a password is known by other means, such as through insecure storage of the password on the PC, or through malware.
New Methods
The following specific measures are implemented for Password Check of the Data Protection Authority of the Canton of Zurich:
- All checks are performed in the browser of the user. No passwords are transmitted or held on a server.
- Checking is done in real time. While entering the password the user is able to see how the password assessment changes with each additional character.
- Dictionaries are available for Swiss Standard German, Italian, French, Romansch and English, which can be selected by the user.
- Word search recognises known modifications (leet / leetspeak).
- Keyboard patterns are based on the Swiss keyboard.
- The source code and the administration process are publicly accessible (Github Repository).